Centralized Policy Management
The intelligence and power behind the PositivePro™ managed VPN service derives from the Cloud based Policy Manager capabilities (Policy Manager). Policy Manager provides the administrator interface that maintains and enforces security policies for all groups and individual remote access users. It is available from an ordinary web browser with a secure login.
Within the Positive VPN system, it is possible to centrally manage policies, configuration settings and actions for each user. The Policy Manager tells the PositivePro VPN Client, WebTop, or RDA which registry keys, files and processes to monitor and manage.
Policies typically are security-related and allow each company to enforce its own security settings on the remote environment. For example, the company can require that the remote PC must be running a firewall with a particular rule set before remote access to the corporate LAN is allowed. Similarly, it can require that the remote PCs do not permit their drives to be shared while signed onto the system. We have built an engine that permits hundreds of Policies to be pushed to each user, so that the company has maximum flexibility in creating user environments that fit its business needs.
PositivePro Policy Manager
Configuration Settings allow the administrator to configure network, desktop and application settings so the worker's system is optimized for work when signed on to the Positive VPN environment. For example, after the user signs in, his Windows environment and applications such as Microsoft Outlook and Internet Explorer will reconfigure to the appropriate corporate settings (proxy server, mail server, Internet home page, mapped network drives, mapped network print shares, etc.). The Policy Manager keeps track of all original state information, so that upon sign off the user's system is automatically restored to its original condition. With the Positive VPN system, even the most detailed application settings, such as default Homepage or desktop wallpaper, can be managed centrally if so desired by the company.
The Policy Manager is also configured with the appropriate set of Actions for the system to take when violation conditions are discovered. These actions are implemented in real-time, as the Policy Manager is in real-time communication with the Positive VPN Client when a user is signed on to the system. For example, if the firewall or anti-virus software is disabled during a session, the VPN connection could automatically be taken down. Or instead, a warning could simply be sent to either the end-user or the company IT Department. Alternatively, the end-user could be taken to a captive portal with instructions describing how to turn on the firewall. Most Policies and Configuration Settings are associated with a variety of possible Actions, which can be configured on a per-user basis.
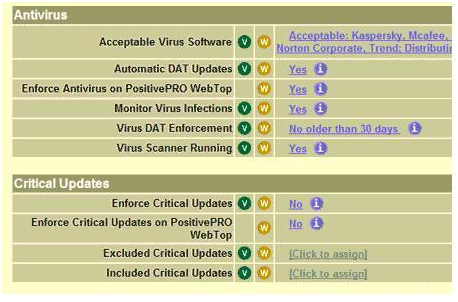
The use of restriction sets makes VPN endpoint security granular without making its administration complicated. Any number of sets can be defined and applied to groups of users or individual users as desired. Each set enforces detailed access controls (in addition to any others in effect) based on the level of security provided by the user's PC. A restriction set can include any of the following criteria (and applicable parameters):
Restriction sets help manage location-based access, such as restricting access to certain files by offsite users. The Policy Manager detects that the user is accessing the corporate VPN from home (even with the same username and password) and prevents remote access to these restricted resources. When a user accesses the VPN from, for example, a public kiosk, the restriction set may authorize access only to e-mail (see the sidebar on PositivePro and Public Kiosks).
This centralized management scheme provides a company an unprecedented ability to maximize the security of its network resources, reduce its support costs, and enable a truly productive work experience from the home or other remote location for its employees.

